Thomas Jefferson Used Encryptionby Wendy McElroySep. 01, 2012 |
Popular 
Russia Advancing in Ukraine at 'Fastest Pace Since Early 2022'

Biden Admin Urges Ukraine to Draft 18-Year-Olds as Russian Gains Accelerate

Israel Bombs Neighborhoods in Lebanon Ahead of Approving Ceasefire

FL State Sen. Randy Fine Celebrated Israel Killing an American - Trump Just Endorsed Him For Congress
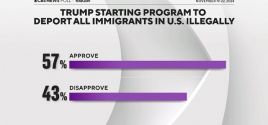
Poll: 57% of Americans Support Trump Starting Program to Deport All Illegal Immigrants
 The encryption of computer data is one of the most powerful tools individuals have to protect themselves against an intrusive state. Encryption is the process of converting data into encoded text produced by an algorithm. To convert the encoded text back to its original form requires either a ‘key’ or tremendous effort. A key is a sequence of numbers that senders typically offer to those they wish to decrypt the protected data. All others must use the ‘tremendous effort’ option. The state wants to be a universal key holder. Otherwise, people could transmit everything from love letters to financial data in a secure and private manner that escapes surveillance. The state argues that encryption offers new and unique protection for terrorists, tax evaders, drug dealers, pedophiles and other miscreants. And, so, new and unique measures must be taken to pull back the dangerous veil of cyber privacy. Nonsense. Encryption is almost as old as communication itself. The root word “cryptography” comes from two ancient Greek words: “crypto” or “hidden”; and, “graphia” or “writing.” Encryption’s main purpose is to shield information from those who would use it in an unwanted manner. Knowledge has always been power and those who seek power have always commanded or censored access to knowledge, depending on which action gave them advantage. In America, the tug of war between privacy and forced access to encrypted data is as old as the nation’s formation. As always, forced access was executed by authorities against individuals. In 1785, a resolution authorized the secretary of the Department of Foreign Affairs to open and inspect any mail that related to the safety and interests of the United States. The ensuing inspections caused prominent men, like George Washington, to complain of mail tampering. According to various historians, it also led James Madison, Thomas Jefferson and James Monroe to correspond in code. That is, they encrypted their letters to preserve the privacy of their political discussions. The need for Founding Fathers to encrypt their correspondence is high irony. The intrusive post office against which they rebelled had been established specifically to provide a free flow of political opinion. In the 1770′s, Sam Adams urged the 13 colonies to create an independent postal system because the existing post office, established by the British, acted as a barrier to the spread of rebellious sentiment. Dorothy Ganfield Fowler in her book Unmailable: Congress and the Post Office observed, “He [Adams] claimed the colonial post office was made use of for the purpose of stopping the ‘Channels of publick Intelligence and so in Effect of aiding the measures of Tyranny.’” Alas, the more government changes, the more oppression remains the same. Soon the Continental Congress itself wanted to declare some types of matter ‘unmailable’ because their content were deemed dangerous. Anti-Federalist letters and periodicals became one of the first types of information to become de facto unmailable. (Anti-federalists resisted centralized government and rejected a Constitution without a Bill of Rights.) During the ratification debates on the Constitution, the Anti-Federalists were unable to circulate their material through the Federalist-controlled post office. Throughout history, encryption and the control of information has been particularly important during times of war. Prior to and during the Civil War, for example, both the North and South banned just about everything deemed to be ‘seditious.’ Private communication in America has never recovered. Recent history is rife with purely political postal measures such as the “Cunningham Amendment” (1962) which restricted the circulation of communist literature that originated in a foreign country. The American government has always realized the political importance of controlling the flow of information. In the 1770s, communication occurred primarily through postal routes maintained by horseback riders. Today, we communicate through packets of data beamed across phone lines; the internet is the modern equivalent of the Pony Express. The difference in the transmission mode is irrelevant to the political principles involved. The key questions are, “who owns your personal information?” and “who has the right to access it?” On May 6, 1999, the Ninth Circuit Court of Appeals offered answers. The court ruled that federal restrictions on encryption violate the First Amendment: specifically, they constitute prior restraint and may limit the freedom of the press (Daniel J. Bernstein v. US Department of Justice). In the decision, Judge Betty Fletcher stated, “The availability and use of secure encryption may…reclaim some portion of the privacy we have lost. Government efforts to control encryption thus may well implicate not only the First Amendment rights…but also the constitutional rights of each of us as potential recipients of encryption’s bounty.” Since then, the government has sidestepped the ruling, sometimes quietly, sometimes under the aegis of other laws. For example, the Clinton Administration required a one-time technical review of encryption software as a precondition to its export. Such maneuvers are not a new response to a new threat. They are the same tactics of which George Washington complained, the same ones that drove Thomas Jefferson to use code. _ Wendy McElroy is Author, lecturer, and freelance writer, and a senior associate of the Laissez Faire Club. |



